{/}
<about_me>
...Karan Vyas, a Cybersecurity Analyst and Certified Ethical Hacker, excels in incident response, vulnerability management, and cloud security. He merges strategic leadership with technical expertise, drawing from his proficiency in Python, SQL, Linux, and the NIST and MITRE frameworks.
...I have over 5 years of experience in Cybersecurity field, with a strong background in both security technologies and GRC.
…With over five years of experience in the cybersecurity field, I bring a balanced blend of technical acumen and strategic insight. Specialized in Digital Forensics and Incident Response (DFIR), I have a strong proficiency in essential cybersecurity tools such as Nikto, Metasploit, Wireshark, and Burp Suite. I also offer in-depth expertise in the use of Python, SQL, and Linux for various security applications. My knowledge and application of NIST and MITRE frameworks have consistently aided in effective risk management and incident response, especially in my roles at esteemed organizations like Google and Deloitte. Beyond the technical spectrum, I’m known for my strategic leadership, analytical thinking, and an ability to successfully recover and restore digital assets following a security incident. My contributions and achievements have been recognized on notable platforms like HackerNoon and TheHackerNews, underscoring my commitment to the cybersecurity domain.
(!)
<portfolio>
...Delve into my diverse portfolio, where my skills and expertise as a Cybersecurity Analyst come to life. Each project showcases my proficiency in digital forensics, incident response, and effective utilization of cutting-edge cybersecurity tools. Discover the depth of my experience and the real-world impact of my work.
{ Cosmic Security Dashboard }
//...This security dashboard provides complete cybersecurity solution that a website needs includes SQL Injection alert, DDOS alters, brute force detailed report with IP addresses.
{ Cybersecurity Tools }
//...Complete list of all security tools such as encryption, decryption, password generator, SSL, HTTPS Checker, MD5 & SHA Generator.
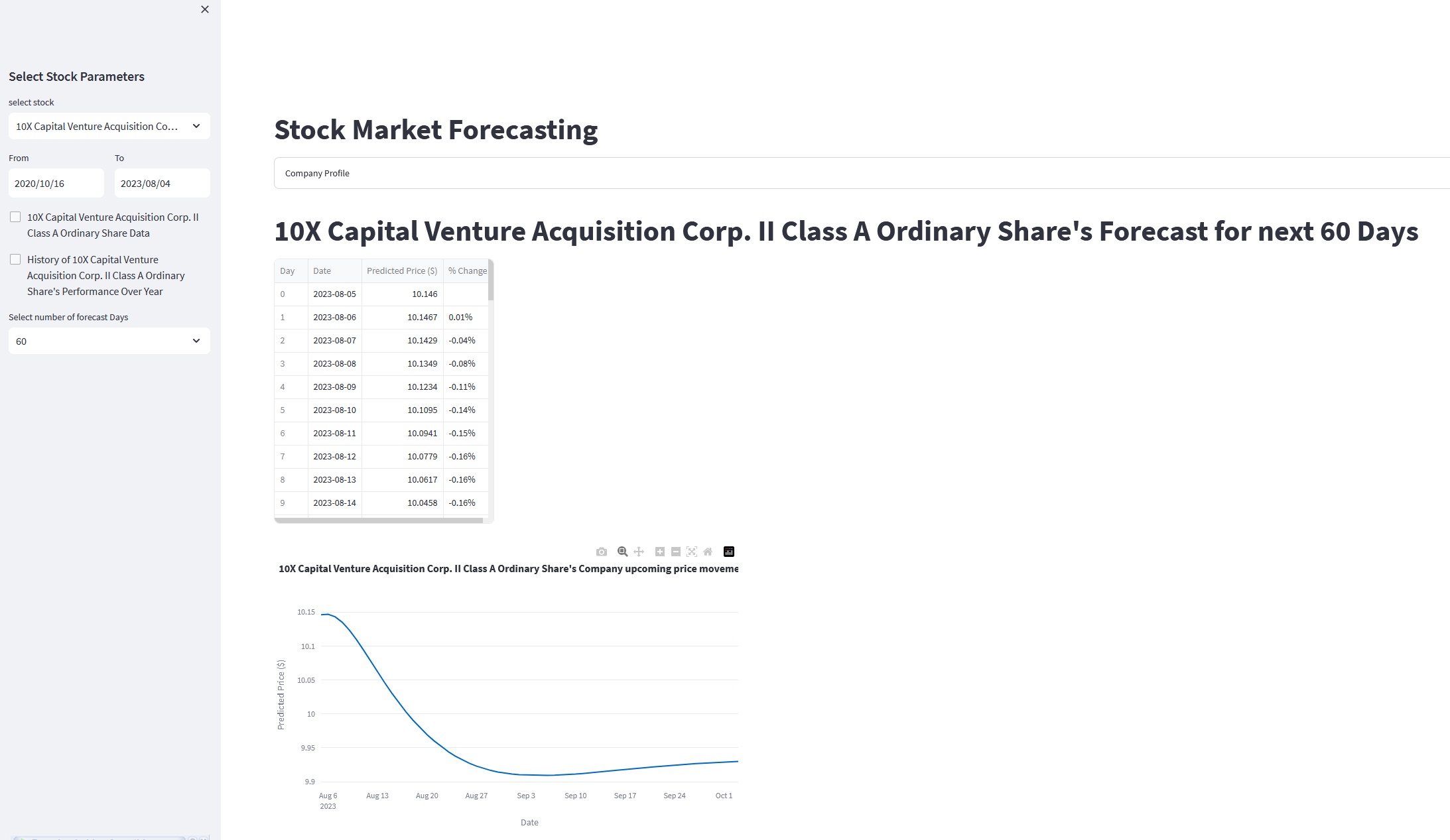
{ Cosmic Trading Forecast }
//...This AI tool can predict the stock pricing for any USA company with upto 90% of accuracy for next 60 days.
{ Project 4 }
//...website design & lorem ipsum dolor sit amet, consectetur adipiscing elit;
{ Project 5 }
//...website design & lorem ipsum dolor sit amet, consectetur adipiscing elit;

{ User Privilege Escalation Detector Velociraptor Artifact }
//...User privilege escalation is a common technique used by attackers to gain higher-level permissions on a system or network by exploiting a bug, design flaw, or configuration oversight in an operating system or software application. The most common form of privilege escalation is when a user's account gets access to functions or commands they were not originally assigned to. This Velociraptor artifact, User Privilege Escalation Detector, aims to monitor and detect instances where a user account is suddenly given elevated permissions in a Windows system.
{#}
<services>
...I have helped govt and organizations to protect themselves against viruses and ransomware attacks.
{" . "}
{" . "}
{" . "}
{" . "}
{" . "}
{*}
<contact_me>
...Feel free to contact me
